Despite the fact that our industry is more than 30 years old we are immature in many ways. There is no clear regulatory framework and no clean guidelines around cybersecurity. In an immature industry technology solutions rather than business and process solutions are often seen as a solution. This is illustrated by a quote from a security luminary, the founding CEO of the RSA security conferince.
“There is too much spending on the wrong things. Security strategies have been driven and sold on fear and compliance issues with spending on perceived rather than genuine threats”- Art Coviello, RSA
One of the most common misquoted pieces of “wisdom” is from a well know early thought leader in the cyber space, “we all know that 80% of attacks are from internal sources” – he went on to spend the next 10 years of his career denying he made this claim, opening his key note talks by expressing that he had never made the statement.
It’s no wonder customers are left not knowing what advice to follow when the world of cybersecurity is full of so many fallacies – with the insights of our expert CEO Etienne Greeff, we’ve uncovered some prevalent ones.
1. The increase in remote working caused by the pandemic, has significantly increased the risk of attacks on remote end points.
This statement has so often been made in recent years and although it is undeniable that there has been an expediential surge in remote working, there is no genuine evidence that it has caused additional risk to end points. In fact, most businesses have actually increased their security level as they embraced cloud services and started focusing on end-point security.
The real area where the risk has increased is the BEC (business email compromise) and phishing. Common example of this are invoice payment requests with different banking details, O365 upgrade emails or an email from your CEO. When in an office environment it is easier to communicate amongst colleagues and quickly identify this as being illegitimate. This is not however a direct link to remote working but to the weaknesses within business systems which are usually countered by the workforce being together.
2. Unpatched systems exposing known vulnerabilities is the most important security issue.
Patch management is an often-repeated mantra with conventional wisdom saying that the most important issue is to make sure systems are patched within a certain timeframe. Vulnerability management is more imperative – understanding what your vulnerabilities are and having systems in place to compensate. Acknowledging that parts of your estate are unpatched and then taking appropriate measures to manage that.
Patch management is pushed but the reality is, you can patch your system to the best of your ability but it still won’t be 100% effective. Even if you patch 80% of your estate within a week after a vulnerability has been discovered, the tools used by threat actors are designed to find that 20% that is not patched.
Of course organisations have to patch to reduce their attack surface but they must also understand that we operate in a world where there will always be vulnerability that we are unable to patch and how then do we do business with an acceptable amount of risk – vulnerability management.
3. Having a combination of different, best-of-breed technology solutions in place increases the level of security.
If organisations use a mixture of different technologies, then these technologies will have different vulnerabilities, therefore spreading the risk. However, most variants of the same types of technology, like firewalls, are built on the same principles using common libraries making them susceptible to the same vulnerabilities, therefore it doesn’t really add any value. It is creating complexity and management difficulties therefore actually decreasing the level of security.
Which goes hand in hand with the notion that organisations need to use best of breed technology for higher level of security. By having best of breed technology companies are actually only adding complexity and usually users won’t utilise all the functionality of the devices they buy.
It would be more beneficial to have a single platform where multiple security solutions can be managed, giving single pane of glass visibility. By prioritising the consolidation of solutions, organisations can reduce the number of people required to manage them, the amount of money spent and free up budget for other network areas in return. Organisations should ask themselves the question of best-in-breed vs best-in-need.
4. Protection defines the maturity of a cybersecurity strategy.
The cybersecurity industry is a very immature industry, meaning it is technology lead and threat driven. There is always a new ‘latest and greatest’ built to protect against the threats we see industry wide, which has created an unbalanced spend against the five pillars of a cybersecurity strategy; identify, protect, detect, respond, recover (diagram 1).
Diagram 1
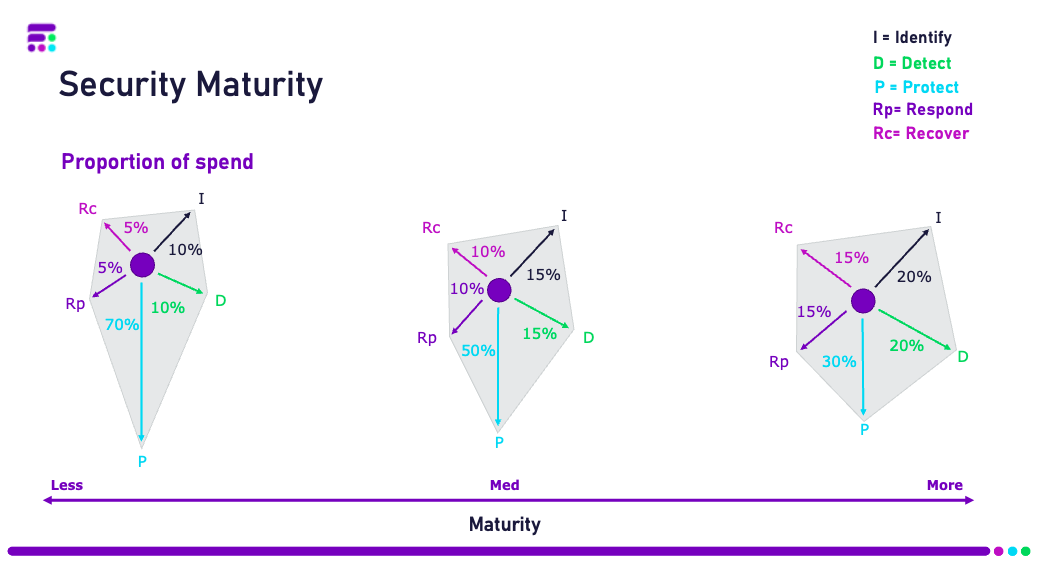
Security maturity can be measured by the distribution of spend across these five areas. An organisation with an immature cybersecurity strategy will spend majority of their money on protection, the latest and greatest or ‘shiny new mouse traps’ (Etienne Greeff, CRN). Little investment is made into understanding and detecting an occurring threat, nor how to then respond and recover from an attack. This is a factor in the devastating success of ransomware, businesses did not have sufficient incident response plans in place.
In an ideal world spend needs to be balanced and almost equal across the five areas, as seen in diagram 1. Spend will never be completely balanced due to the expense of technology being higher than the other areas – but an organisations ability in these five areas needs to be equal. E.g. the ability to understand and detect where threat actors might attack you from is as important as the ability to protect against it when they do.
Come and talk to us about how to balance spend to achieve a mature cybersecurity strategy. Make use of our expert team of trusted advisors through our smart and agile advice.