Exploring this claim
You would be surprised how easily you can assess the maturity of an organisation’s cybersecurity strategy. The biggest tell-tale sign? A massive spend on protection technology, with a far lower emphasis on the other components of a truly stable cybersecurity policy.
What some businesses fail to realise is, cybersecurity isn’t all about protection. It’s a critical element, yes, but without the other four pillars, organisations could quickly find themselves in hot water.
Debunking this myth
The cybersecurity industry is a very immature industry in general, meaning it is technology lead and threat driven. There is always a new ‘latest and greatest’ built to protect against the threats we see industry wide, which has created an unbalanced spend against the five pillars of a cybersecurity strategy; assess, detect, protect, respond, recover.
Yes, these new protection technologies are shiny and exciting, and certainly serve a very important purpose, but if an organisation places the majority of its spend here, there can then be little money left to put towards understanding risks, detecting behaviour, responding and recovering.
Take global shipping giant Maersk as an example. When the NotPetya attack hit in 2017, it brought the company to its knees, as well as countless other organisations around the globe. It even took the radiation monitoring system at the Chernobyl Nuclear Plant offline. When rebuilding the servers, staff quickly realised that there was no clean backup of the company’s domain controllers. Only by a sheer stroke of luck, a blackout at Maersk’s Ghana office had knocked the server offline prior to the NotPetya attack, disconnecting it from the network. It contained a single clean copy of the company’s domain controller data. Maersk estimated that NotPetya had cost the company between $250 million and $300 million by this point. Had Maersk put more emphasis on the ‘recover’ element of their cybersecurity strategy, they wouldn’t have been saved by just luck.
The solution
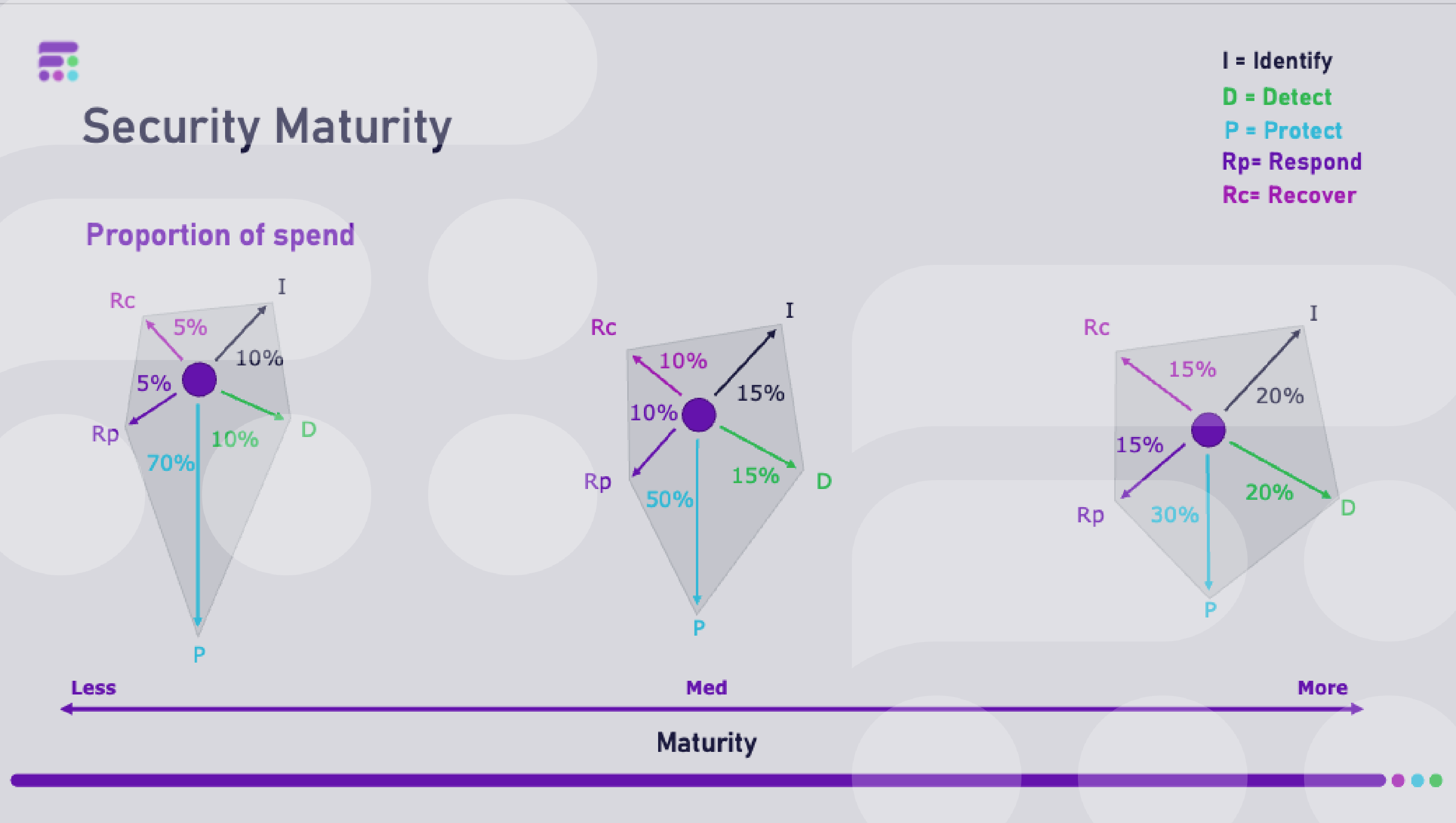
In an ideal world, organisations need a balanced and almost equal spend across the five areas, as seen in diagram 1. Spend will never be completely balanced due to the sheer expense of protection technology being higher than the other areas – but the organisation’s ability in these five areas needs to be equal. E.g. the ability to understand and detect where threat actors might attack you is as important as the ability to protect against it when they do.
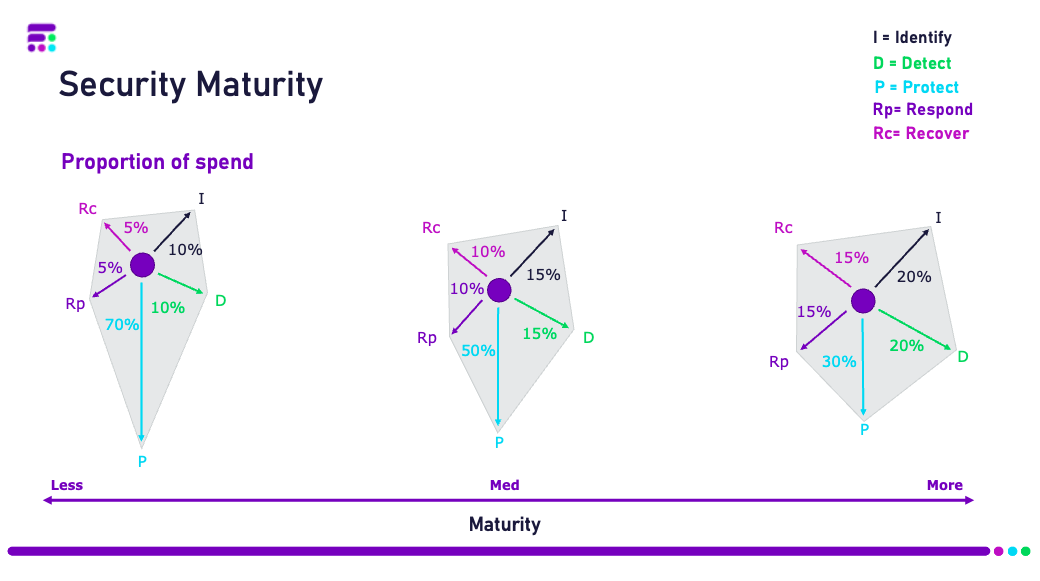
All organisations, no matter how big or small, should adopt a cybersecurity maturity model to assess their current status, and how they can reach the next step or simply create a more even balance of their abilities.
Improving cybersecurity maturity doesn’t happen quickly, but it has to happen to survive amid the ever evolving digital landscape and emerging cyberthreats.
For a security maturity assessment of your business and advice on how to create a robust cybersecurity strategy, contact us here.
Want to know more about how letting the NIST framework guide assessment and investment? Register for your webinar here!