Cybersecurity – How are we getting it so wrong?
Being and staying cybersecure is not easy and so often we’re not getting it right, with even high-profile companies failing. The increasing number of breaches we see in the headlines is testament to the fact that we must be doing something wrong.
“Businesses urged to boost cyber standards as new data reveals nearly a third of firms suffering cyber-attacks every week” says Gov.uk.
In the start of this year alone we have seen some prominent breaches: Royal Mail, JD Sports, T-Mobile and Arnold Clark to name a few.
The board doesn’t get cybersecurity, cybersecurity doesn’t get the board
Although the shock factor of these breaches may be fading, financial impacts, disruption to business operations and long-lasting reputational damage very much remains. The board of directors most definitely care about the impacts of a cyber-attack, but they don’t necessary understand the methods and measures required to achieve a strong cybersecurity posture. And generally, this lack of understanding is reciprocated by the cyber team towards the board.
Let’s consider the scenario: The board will refer to tangible items such as the cybersecurity standards they follow, the resources allocated to it as a function and the budget invested in these efforts but not the genuine risk to the business involved.
So how do businesses translate cybersecurity to the board?
NIST – the internationally recognised standard
By following an internationally recognised standard that is balanced and not overly complicated, businesses can get an accurate reading on how mature their cybersecurity posture is. Being a voluntary framework, there is no rigid pass or fail. It is all about identifying risks, mitigation strategies and measuring how well embedded these mitigations are within the businesses processes and procedures.
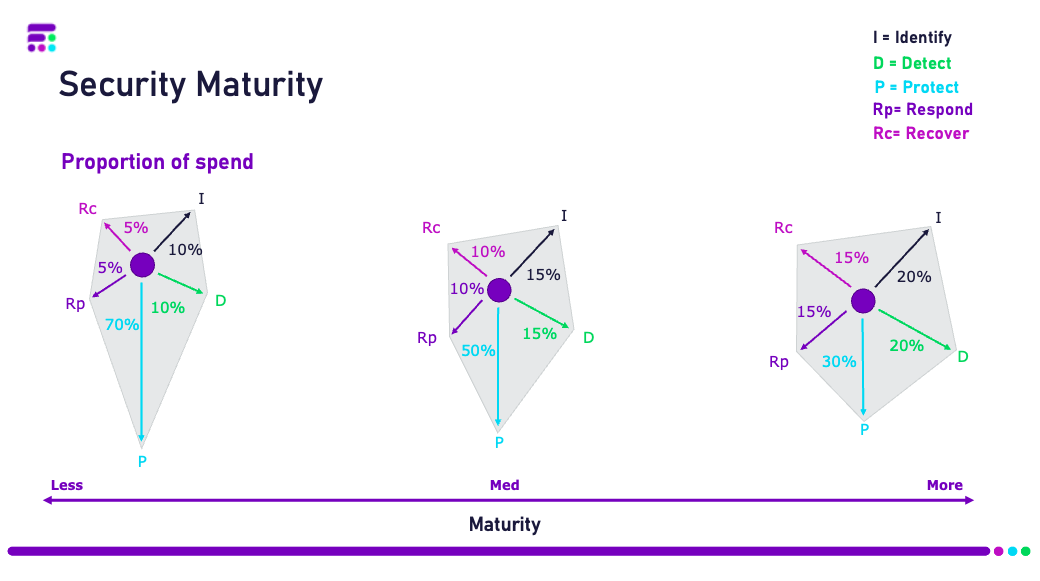
The NIST methodology breaks cybersecurity down into five equally important pillars: Identify, Protect, Detect, Respond and Recover. Businesses need to understand their capabilities and the impact of investment across these pillars.
Why are all five pillars so important when dealing with cyber risk?
Identify: By having understanding and visibility of their estate businesses can build a protection and detection strategy from an informed position. Not fully understanding your digital footprint and the associated risks can cause gaps in overall cybersecurity strategy.
Protect: Technology does play a big part in protecting businesses from risk, however it is important that this technology is deployed in a strategic way to ensure that key assets identified are protected. This ensures a greater return on investment for businesses security spend. From identifying your key assets, and the associated risks, businesses can ensure they are putting their investments into the best areas.
Detect: It is important not to get complacent. Even with a good understanding of our assets and the associated risks, and with a solid protection strategy, things can still go wrong. Having a strong detection strategy will allow business to reduce their Mean Time to Detect (MTTD). Detecting any suspicious activities early, reduces the time of unauthorised access on their infrastructure, which in turn reduces the damage caused.
Respond: Being able to detect suspicious and malicious behaviour is the first step. Detection needs to trigger a well thought out and practiced Incident Response Plan. Having reduced the businesses MTTD, the next target is to reduce the Mean Time to Respond (MTTR). Responding swiftly to detections will enable the businesses first responders to contain a breach efficiently and reduce the damage caused.
Recover: Having contained a breach, the next phase is to recover. A well-designed Recovery Plan can significantly reduce the time to restore full business operation. Recovery not only covers the restoration of systems, data and services, but also public relations management to limit the impact to business reputation.
Why businesses should care about assessing their posture in these five pillars
Putting this very precise methodology to work we’ve created our Cybersecurity Posture Assessment (CPA), with a direct criterion for assessing maturity in each pillar. Delivering clear scoring and improvement opportunities, whilst benchmarking businesses against the industry.
Our CPA is a tool to identify where the gaps are, the impact of potential investments into the different pillars, with continuous assessment making cybersecurity progression measurable. Therefore, enabling businesses to translate this to the board.
In terms of accuracy and value, this methodical approach exceeds that of the dated alternative, so pertinently put by our CEO Etienne Greeff, ‘cover your arse IT’. Investing budget into the ‘latest and greatest’ cybersecurity technology, simply to protect from criticism when a cybercriminal does no doubt succeed in attacking the business. Cybersecurity resources are scarce – businesses need to be certain they are investing their valuable resources strategically, in the areas that will have the most impact and tangible results.
Would you would like to explore how we can support you to make cybersecurity tangible for the board? Watch out on-demand webinar here.